Mandar Phadke is an Engineering graduate from the University of Bombay and a postgraduate in Management from LaTrobe University, Australia. He is currently heading Abhisam Software, a company involved in developing e- learning programs, certifications and provides consulting in areas like Industrial Cybersecurity, Process Safety, Functional Safety, Hazardous Areas & Industrial IoT. Prior to Abhisam, Mandar has worked for more than two decades in the chemical process industry, for marquee multinational companies such as Bayer and Lanxess, in leadership roles related to project design, engineering, commissioning, operations, maintenance, safety and decommissioning.

The year 2020 was unusual, mainly due to the COVID 19 pandemic that disrupted normal life. As regards Industrial Cybersecurity, there were a few Industrial Cybersecurity incidents, as well as quite a few positive developments too, which I list below. Further on, I will also show you my wishlist for the Year 2021 and beyond.
Some Developments in the Year 2020
1. Cyberattacks on Israeli water infrastructure.
These were not one single attack, but multiple ones on different types of water related infrastructure, such as agricultural pumps, as well as trying to manipulate Chlorination systems that supply drinking water to cities. The attackers tried to increase the Chlorine level beyond safe limits and if successful, could have caused mild poisoning to the consumers.
2. Former US President Donald Trump issuing an Executive Order
Former US President Donald Trump issued an Executive Order regarding cyber security of the bulk electric supply and power grid in May 2020.
This also included among other things securing the electric power utilities from supply chain attacks. This was after he extended the National Cyber emergency state in March 2020.
3. MITRE ATT&CK for ICS being made publicly available.
The MITRE ATT&CK was earlier available only for Enterprise Cybersecurity but they have also now developed an ICS specific matrix.
4. The US Cybersecurity and Infrastructure Security Agency (CISA) released its five year Industrial Control Systems security strategy
According to the agency “A Unified Initiative, is a multi-year, focused approach to improve CISA’s ability to anticipate, prioritize, and manage national-level ICS risk. Through this “One CISA” initiative, CISA will work with critical infrastructure (CI) owners and operators to build ICS security capabilities that directly empower ICS stakeholders to secure their operations against ICS threats”.
5. ISA 99 committee released the ISA/IEC 62443-3-2 which is one part of the multi-part ISA/ IEC 62443 standard, that deals with risk assessment of Industrial Control Systems.
6. UL (Underwriters Laboratories) formally announced that they have launched a system to assess cybersecurity in the supply chain.
Although it is not exclusively for ICS cyber security, yet it could be used as an alternative to the ISA Secure system to ensure that Industrial Automation system components are secure and do not become backdoors that can compromise ICS security of the host system.
7. Sanctions against Russian agency for suspected TRITON involvement
In Oct 2020, the US Government’s Department of the Treasury’s Office of Foreign Assets Control (OFAC) designated, pursuant to Section 224 of the Countering America’s Adversaries Through Sanctions Act (CAATSA), a Russian government research institution that is connected to the destructive Triton malware. As you probably know by now, the TRITON malware targets TRICONEX Safety Logic Solvers and was first discovered sometime in the year 2017 in a Saudi Arabian petrochemicals plant. It did not cause any kind of asset damage or accident, but the implications made plant owners and operators, pretty nervous.
8. Secure Coding practices for PLCs
A need was felt for defining and listing secure coding practices for PLCs. An online forum named “Top 20 list of PLC secure coding practices and supporting documentation for engineers, security professionals and management” was set up. The forum is hosted by ISA.
The above list is a compilation of major Industrial Cybersecurity related events in 2020. Now we will take a look at my wish list for the year 2021 and beyond.
Wishlist for the year 2021 and beyond
There are some ambitious (and some might argue not very doable things in the span of one year) in the list. However, one must start somewhere. Hopefully, somebody or some organization can take these up.
1. Control System Vulnerability Reporting Platform & Knowledge Repository
We should have an alternate way to report, collate and share information among stakeholders, including asset owners and system integrators, at a global level. Perhaps, professional non-governmental bodies, like ISA, IEEE or IET should take the initiative, so that the platform/repository is vendor neutral, as well as government neutral. There should be a way to anonymously share information not only about known vulnerabilities, but also about actual incidents, suspected incidents, detection of counterfeit devices (and/or malware loaded booby trapped components). This should be updated as frequently as possible and monitored by plant and asset owners, so that they can take quick, corrective actions. To the best of my knowledge, there is no such system now. I guess the main roadblock in getting this done is funding and no possible ROI for the investors, unless subscriptions can pay for it. At present the US Government agency CISA is playing a similar role, but it is limited to listing vulnerabilities and alerts, which are not only ICS specific. It depends on various vendors and others to spot vulnerabilities and report them. Presumably, these are addressed by vendors via updates (patches).
2. Securing Industrial Systems against Supply Chain attacks
There should be a better way to secure Industrial Systems against supply chain attacks. As of now, there does not seem to any specific standard for this. ISA Secure is a good initiative, but it can be better. The owner of the IACS should also be sure that no counterfeit products are being used in their system.
3. Automation Services and Software Supply chain resilience
The term “Supply chain”, should include not just physical devices that are used in Industrial Automation and Safety systems, but also software programs and services, including the individual persons who provide these.
As of today, software patches and programs have been covered in IEC TR 62443-2-3:2015 and system integrator/automation vendor services have been covered in IEC 62443-2-4:2015 (and amended in 2017). These are steps in the right direction but there should be commonly agreed due diligence practices, as regarding background checks of personnel who work on these systems as well as vetting of their equipment.
How do you know that the system integrator’s engineer who normally maintains your system, does not have a compromised laptop that he plugs into your automation system? Are these people aware of Industrial Cybersecurity? Do they diligently follow good practices?
Beginning 2021 we should aim towards making all participants of the Industrial automation supply aware about Industrial Cybersecurity and also be competent in the subject. Once this is done, we can be sure that the Industrial Automation supply chain has become more resilient towards thwarting attacks.
4. Secure Automation network protocols (e.g. Secure Fieldbus)
In my opinion (and you can of course disagree with it), the Zone and Conduit philosophy of protection as given in ISA/IEC 62443 for IACS is at best a stop-gap arrangement. Once a malware breaks through a DMZ/firewall into a Zone, it can pretty much own everything inside the Zone. This is because almost none of the Instrumentation & Control Systems protocols used in the process industry, have authentication and encryption at the field level, or many times even at the controller network level. Hence, we do need a new automation protocol at the field level that has authentication, as well as encryption. The Industrial IoT phenomenon presents us with such an opportunity and again, professional engineering associations like ISA or IEEE should take the initiative.
5. A generally accepted taxonomy about Industrial Cybersecurity terms
Taxonomy and definitions, regarding Industrial Cybersecurity seem to be still in development. For example, recently a poll was carried on LinkedIn by ORIGNIX Inc asking people what they thought about the terms, OT and ICS and the results were as given in the image below.
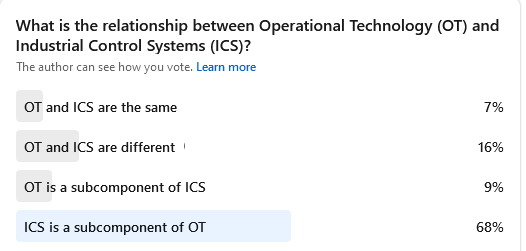
Since the poll responses have been from mostly people in the Industrial cybersecurity field, it is evident that there are varied ideas of what constitutes OT and ICS sometimes even diametrically opposite of each other (e.g. OT is a subcomponent of ICS versus ICS is a subcomponent of OT).
This is troubling because if we do not agree about what these terms mean, then it will be difficult to have conversations, as well as contracts, between owner/operators, automation and safety system vendors/system integrators, engineering design companies and others.
A well agreed system of definitions and a commonly accepted Taxonomy is therefore urgently needed.

NEWSLETTER
TRENDING ON PRO MFG
MORE FROM THE SECTION








